|
|
 |
|
Policy based
Firewall with: |
|
|
Today the Internet is a vital tool for business
communication. Many companies communicate with
customers, partners and affiliates via the Internet.
This is the reason of the Internet security becomes a
problem of paramount importance. To keep customers’ and
partners’confidence companies have to secure sensitive
information and network resources properly.
You need Z-2TM – policy
based firewall to protect sensitive corporate, partners’
and customers’ information against being accessible
beyond the appropriate relationship boundaries. Z-2TM
controls and filters corporate network flows on both IP
and Application layers. It detects attacks, unauthorized
accesses to internal corporate information resources and
other violations of the network security policy and
suppresses them automatically. Z-2TM easily integrates
with virus scanners and content security solutions to
protect companies against viral infection, spam and
forbidden files.Z-2TM has an advanced authentication
server that provides users with the secure access to
corporate information resources. |
| |
Z-2TM provides companies with: |
|
Z-2TM key features: |
|
Total
control over incoming and outgoing information flows
Detection
and prevention of network intrusions
Concealing
of the corporate network structure
User
identification and authentication
Fine-grain
control of access to corporate resources and services
Checking
information flows for viruses
Analyzing
and reporting on network security activity
Deployment
of the network security policies |
Built-in
Intrusion Detection System (IDS)
Filtering
on Network, Transport and Application layers
Integrated
Network Addresses Translation (NAT) technology
Advanced
user authentication
Centralized
management of security policies
Java-based GUI
|
|
|
|
Multilayer
Filtering System |
|
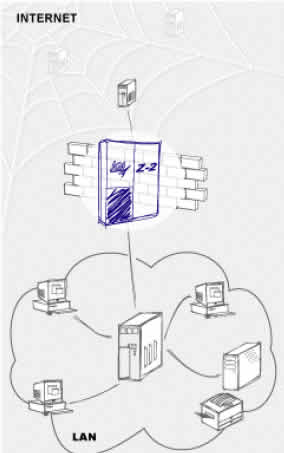
Z-2TM performs data filtering on
Network, Transport and Application layers. Z-2TM checks the data
against criteria specified by the security administrator and
executes an appropriate action (e.g., proceeds with data
transfer). Z-2TM provides advanced authentication mechanism that
enables protecting from passive attacks (e.g., packet sniffing
for interception of user identifiers and passwords). Z-2TM
performs Network Address Translation according to specified
rules. This feature prevents the structure of the internal
network from being discovered by outsiders. It allows companies
to use arbitrary IP addresses within the internal network. To
prevent denial of service (DoS) attacks, Z-2TM limits the number
of requests processed concurrently. Z-2TM can be configured to
react automatically to unauthorized actions or other policy
violations (e.g., notifying the administrator). This assures
timely responses to violations and helps companies to minimize
eventual losses. Z-2TM logs all network security activity:
requests for access to corporate resources, results of requests,
detected and prevented security violations, etc. Z-2TM includes
tools for analysis of logged information and reporting the
results.
|
PLATFORMS: |
|
Sun Solaris/SPARC |
Sun
Solaris/x86 |
Security
Appliance |
|
Built-in extensible
authentication server:
- Identifies and authenticates
users that request for access to corporate services by
reusable or one-time passwords
- Allow security administrator
to add other authentication modules by using of pluggable
authentication module (PAM) without modifying the server
configuration
High reliability of Z-2TM is
ensured by:
- Built-in logging and
auditing system
- Run-time monitoring of
software integrity and environment
- Built-in backup and recovery
system
Internal security is ensured
by:
- Granting different access
privileges to different administrators
- Granting access to
authorized administrators only
- Monitoring and logging all
administrators actions
Balancing protection and
performance:
- High performance
application-layer filtering (implemented at the kernel
level) fits for high-speed channels
Integration with other
security solutions:
- Spam-blocking systems
- VPNs
- Virus scanners
- Content filtering tools
|
|
|
فهرست
قیمت نرم افزار |
 |
|
|
ارسال كاتالوگ و اطلاعات مورد نياز در اين صفحه به آدرس
پست
الكترونيكي شما
|
|
| |
|
Copyright © 2002 BaniSaz International Co, Dubai, U.A.E.,
All rights reserved.
|
